
Global threat landscape
Introduction to the Cybersecurity Threat Landscape : threat actors, typical targets and common attack methods.
Complete the following nine modules to earn your personalized completion certificate. Each module lasts less than five minutes and ends with a quiz.
It is strongly recommended to watch modules in their original order. You can resume your training later by taking note of your session code or creating an account.


Introduction to the Cybersecurity Threat Landscape : threat actors, typical targets and common attack methods.
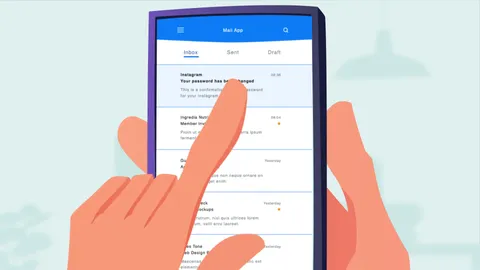
Introduction to Phishing : Why do criminals use phishing, what does it look like and what behaviors should you adopt to protect yourself.

Introduction to Password security : common password attacks, consequences of stolen credentials and behaviors to adopt in order to protect yourself.

Introduction to MFA (Multi Factor Authentication) : Most common MFA methods, tricks attackers use to bypass MFA and behaviors to adopt and avoid.

Introduction to the concept of Malware : Types of malware and their purpose, principal infection vectors and behaviors to adopt to reduce risk.
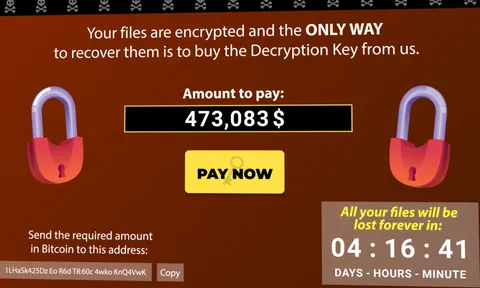
Introduction to Ransomware : criminal group operations, attack methods and potential consequences on organizations.

Introduction to Device Security concepts : trusted vs. untrusted devices, physical access security and malicious external devices.
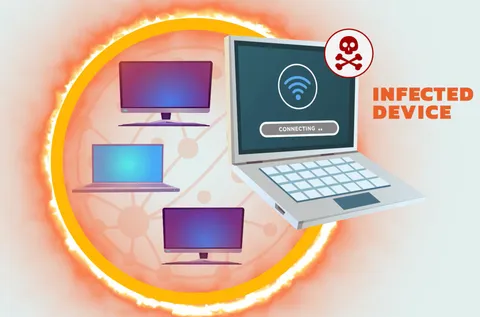
Introduction to Network Security concepts : trusted vs untrusted networks, encryption, public WIFI and VPNs.

Introduction to Data Security and Privacy concepts : Confidentiality, Private Data, Permissions and Safe Data Handling.